Twitters Lax Security
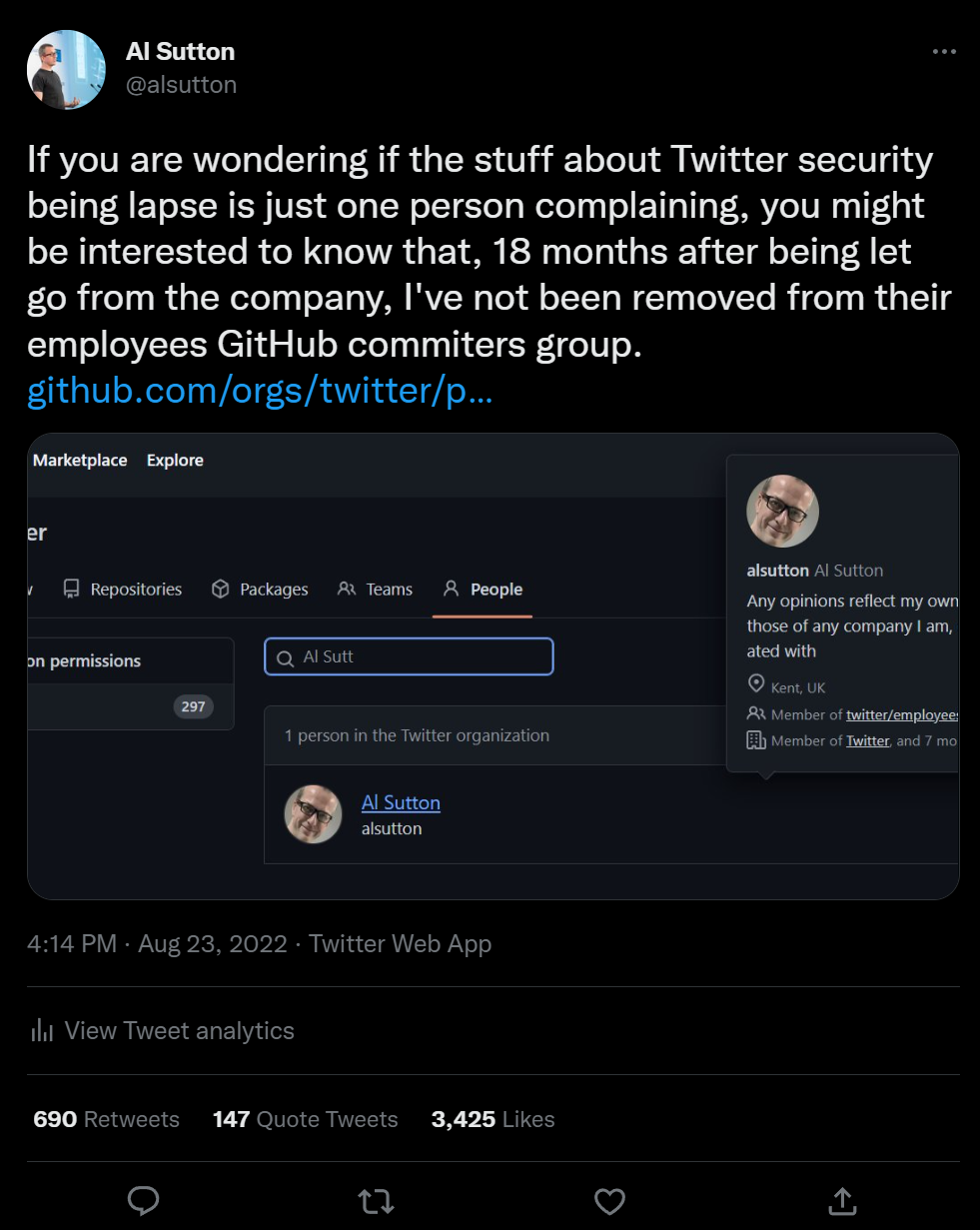
If you are wondering if the claims about Twitter security being lax is just one person complaining, you might be interested to know that, 18 months after being let go from the company, I had still not been removed from their employees GitHub committers group.
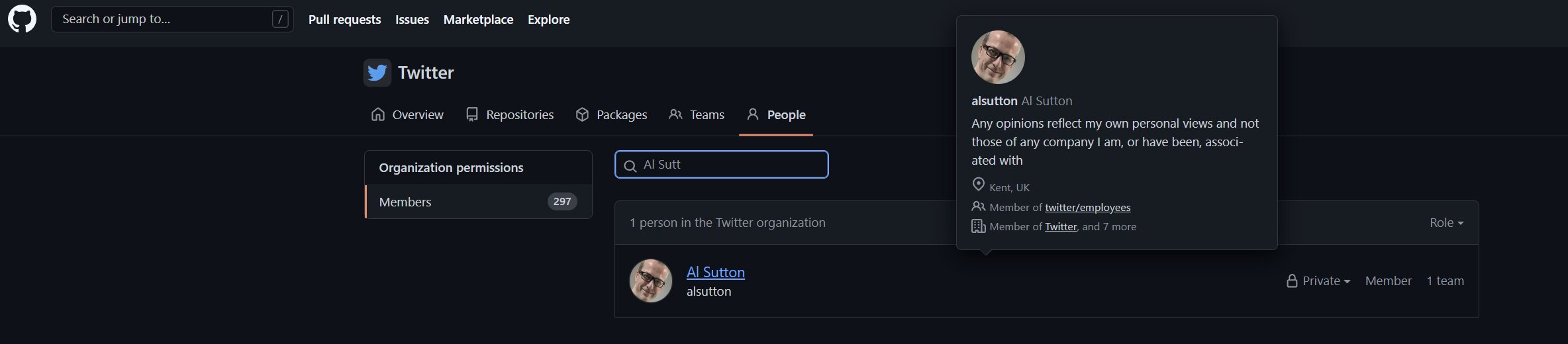
My access was confirmed by a third party, and, during that 18 month period I had access to private repositories as well as the list of Twitter employees who were also part of that group, but had chosen not to make their membership public.
This is concerning on multiple levels;
- Employees who are let-go should not retain access to company systems. They are the most likely to hold a grudge and copy/modify source code.
- It corroborates Mudge’s claims Twitters security controls are not up to industry expectations.
- It indicates a low level of investment in information security because automating the detection of this kind of thing is relatively simple.
- Access to a non-public list of Twitter employees, who were also part of that group, gives a great starting point for a social engineering attack.
There were some claims, particularly by one Twitter employee, that this wasn’t serious. This is a concerning attempt to down-play the potential seriousness of this mistake, and is in-line with Twitters original PR strategy towards Mudge of attacking the person, not addressing the claims. Fortunately I could show I had access to a private fork of a public open source project where Twitter had being committing proprietary code in relation to their embedded devices.
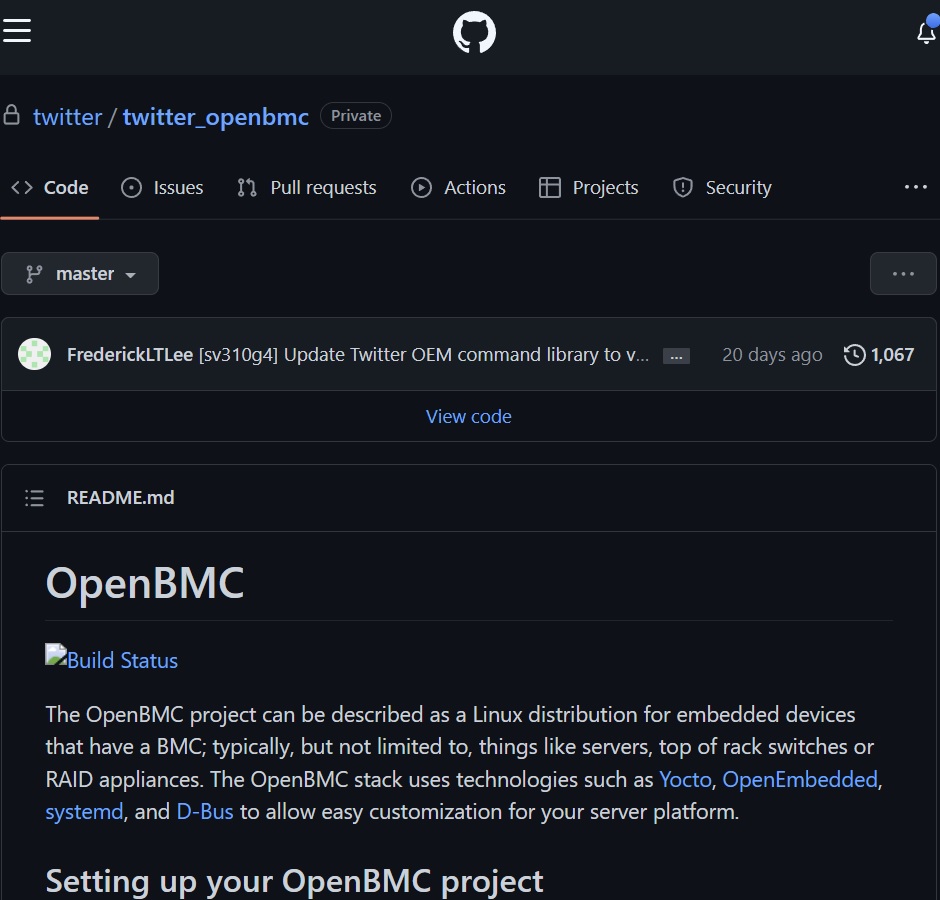
After a few hours, and after Twitter being contacted about my situation, I was removed from that GitHub group, as I should have been 18 months before.
It was an interesting experience seeing the original Tweet where I mentioned my access become so popular, and it was great to see the level of interest folk showed in the security of a site they commonly use. The initial Tweet also became the most popular Tweet I had ever made, with more likes that I’d had followers.